In October 2008, Satoshi Nakamoto published the first description of blockchain, the technology behind the peer-to-peer bitcoin payment network. A few dozen techno-geeks around the world knew about bitcoin and the blockchain. But most people’s attention was focused on the recently launched AppStore and the release of the first Android smartphone.
Now let’s rewind to our own time and see that various blockchains store corporate and personal information, entertainment content and, most importantly, millions of transactions involving cryptocurrencies and traditional financial assets.
In this lesson, we will explore what blockchain technology is, how it works, and how it is fundamentally different from other solutions for recording and storing data.
What is Blockchain?
Blockchain is a distributed database that contains information about all actions (transactions) performed by users. This technology was first used in the Bitcoin payment network in 2008.
The main difference between blockchain and other distributed ledger technology (DLT) solutions is its unique architecture. Its characteristics are embedded in the very name of the technology: block – block, and chain – chain, where:
Block is a “package” of information. In the case of cryptocurrency, we are talking about a specific type of data, namely transactions;
chain is the link between blocks. Each successive block contains information about the previous one, so that from block to block you can see all the actions in the network back to the first (genesis) transaction.
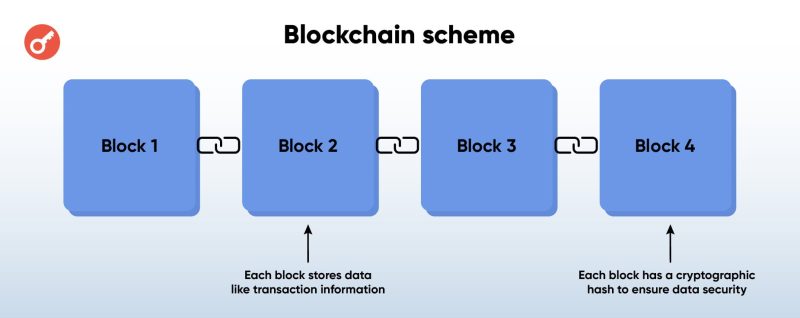
To better understand the overall structure of a decentralised network, imagine a notebook in which each page is a block of transaction records. And the notebook is a set of linked blocks, a blockchain.
Information in a blockchain is publicly stored and distributed. Instead of a single server, as in traditional databases, there is a network of multiple nodes, each of which maintains its own copy of the transaction ledger and periodically synchronises with the others. Thus
the complete transaction register is freely available;
copies of this register are written to many servers with equal rights;
all these servers (nodes) are constantly synchronised.
Any user can become part of such a network – it is enough to install a special application (client) and download a copy of the database to his device.
Thanks to this architecture, it is impossible to unilaterally change information; to write new transactions into the blockchain or edit existing ones, all nodes connected to the network must agree (consensus).
In addition, distributed data storage provides resistance to hacking – even if a hacker gains access to one of the nodes and edits a copy of the registry stored on it, at the next synchronisation these changes will be rejected by other network participants and the modified copy will be rolled back to the agreed version.
Note, however, that the above only applies to public blockchains, which are decentralised at a technical and organisational level and operate according to inherently defined rules. There are also private networks where the owner decides who can upload a copy of the ledger and add, store and view data. In the crypto industry, however, private blockchains are the exception rather than the rule.
Blockchain and cryptography
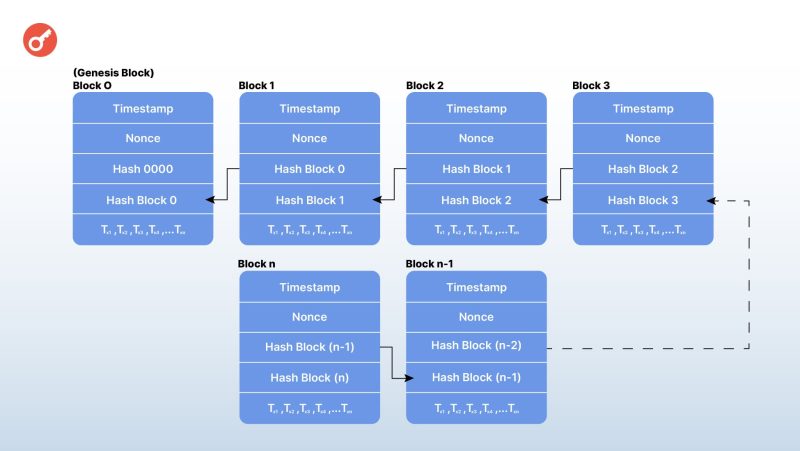
To guarantee the security and immutability of a transaction record, the blockchain algorithm converts it into a special cryptographic cipher – a hash. Each block consists of a header and a list of transactions. The header contains
its hash;
the hash of the previous block
The hash of each transaction;
a timestamp indicating when it was created.
The hash itself looks like a random set of characters and is actually encrypted transaction information. The encryption is performed using a hash function – a special algorithm that can convert any amount of data into a single line of code made up of letters and numbers.
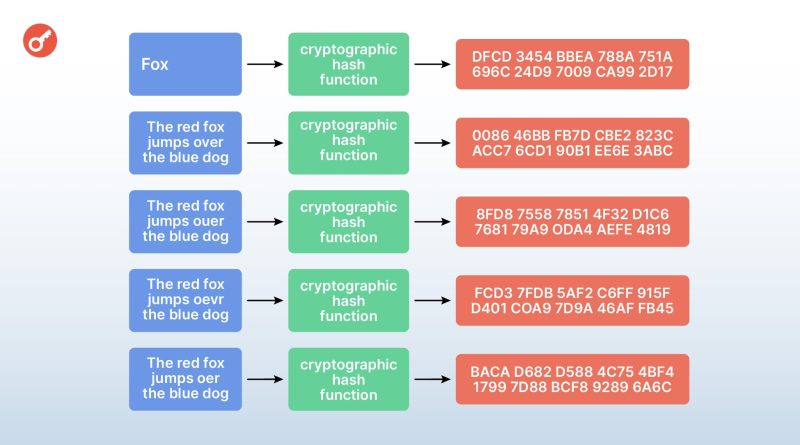
A hash guarantees the integrity of the information, as any change to the input data will produce a new hash that is different from the original. How much a hash generated by the SHA-256 algorithm (used in Bitcoin) can be transformed by changing just one letter is shown below.
Another key component of blockchain storage is the so-called Merkle tree, introduced in the late 1970s by computer scientist Ralph Merkle.
This “tree” shows the structure of the data stored in the blocks as transactions encrypted using a hash function.
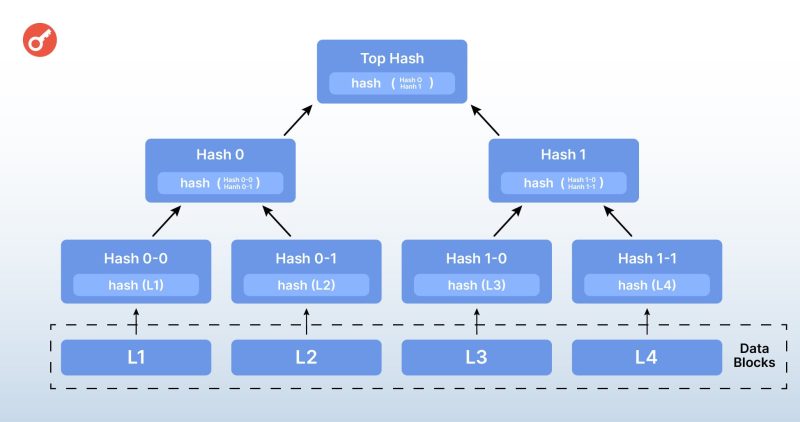
The main value of a Merkle Tree is that it allows for a multi-level data structure in which the information in the lower levels cannot be changed without affecting the upper levels.
In the late 1990s, Stuart Haber and W. Scott Stornetta used Merkle trees to store digital documents securely. And in 2008, the Bitcoin technical documentation described the use of this technology to protect against tampering and alteration of data stored on a decentralised network.
There are now many modifications and types of Merkle trees, with different architectures and based on different hashing algorithms. For example, the anonymous cryptocurrency Monero uses binary hash trees, and the Ethereum team has developed its own version of the technology called Merkle Patricia Trie.
Types of blockchains
The main criterion by which decentralised networks are divided into different types is the consensus algorithm, which defines how nodes interact to negotiate changes to the blockchain.
Two algorithms are the most widely used:
Proof-of-Work (PoW) – a block of data can be added by the node that first performed complex mathematical calculations during the mining process. These calculations are energy-intensive and require a material investment from the node owner, thus ensuring their loyalty. Bitcoin and several other networks use the PoW algorithm;
Proof-of-stake (PoS) – Information is added by special validator nodes that validate the cryptocurrency as proof of loyalty. If the validator tries to enter information that violates the rules of the network, his deposit is confiscated. This algorithm, in various modifications (PoS, DPoS, LPoS), is used by Ethereum and most new blockchains.
However, in addition to PoW and PoS, there are a number of other concepts used by individual cryptocurrency projects. These include Proof of Authority (PoA), Proof of Capacity (PoC) and others.

Apart from the consensus algorithm, decentralised networks can also differ in the programming languages supported, node requirements, data transfer methods and many other parameters. As a result, different blockchains can offer different transaction costs, processing speeds and security. We’ll look at bitcoin and other networks in more detail in our next lessons.
Where blockchain is used?
Technically, blockchain is simply a new way of storing information that can replace any centralised database. However, the architecture and operating principles outlined above make it the most appropriate solution for some areas and technologies.
Payments
Cryptocurrencies are primarily payment networks that allow users to securely transfer digital assets to each other, and are cheaper to maintain than traditional solutions such as SWIFT.
Smart contracts
Modern decentralised networks such as Ethereum can store not only transaction records, but also complex sets of code called smart contracts. A smart contract contains an algorithm of actions, and is the basis for complex applications that are stored and executed entirely on the blockchain.
Public registries
Some countries are testing blockchain as the basis for public land registries, medical data storage and even digital national currency transactions. A good example is the e-gryvnia pilot mentioned at the beginning of this article.
Proof of ownership and copyright
Blockchain data cannot be tampered with or altered, making it much more efficient and secure than existing patent and registration systems, which are based on paper or digitised archives that are centrally stored and unverifiable.
How secure is blockchain?
Because of their architecture, blockchains are resistant to hacking and unauthorised changes aimed at stealing, deleting or editing data. However, public decentralised networks are still potentially vulnerable to some threats.
51% attack
If an attacker manages to take over 51% or more of the nodes, they will be able to approve or reject changes made to the network, for example, authorising the double spending of an asset. However, no major network has yet been able to carry out this attack due to the cost and complexity of implementation.
For example, speaking about bitcoin security in 2015, Andreas Antonopoulos noted that it would take billions of dollars and the coordinated efforts of an entire country to manufacture mining computers to take over the network.
If successful, attackers would be able to open a 10-minute ‘corridor’ to make changes to the database that would cause the blockchain to split into two alternative chains. One will contain a block with the edited data, the other will not. The original network will continue to operate as before, albeit with fewer nodes and less computing power.
Sibyl’s attack
For a transaction to be written to the blockchain, it must be confirmed by multiple nodes. In the bitcoin network, for example, a transaction is not written to the blockchain until it has received at least six confirmations.
The nodes to which the algorithm sends confirmation requests are chosen randomly, but if the total number of nodes is small, there is a chance that an attacker could control all the nodes that receive a confirmation request. This would give them the ability to add a rule-breaking transaction to the blockchain, or refuse to accept honest transactions in order to block or slow down the blockchain.
Other nodes could reject the malicious transaction, again leading to network partitioning. However, there are no known successful Sibylla attacks on public blockchains in demand.
In practice, blockchains are the most secure element of the crypto industry’s infrastructure. The main hacks, data breaches and thefts occur when interacting with various applications and services, such as cryptocurrency exchanges or wallets, but the integrity of the network itself is not compromised.
Challenges and evolution of blockchain
Decentralised networks are developing rapidly, but it is a relatively new technology and there are a number of challenges to its adoption. Ethereum founder Vitalik Buterin has highlighted these weaknesses in what is known as the blockchain trilemma.
It states that any distributed network has three key characteristics – decentralisation, security and scalability. However, traditional blockchain architecture can only provide two of these simultaneously and fully.
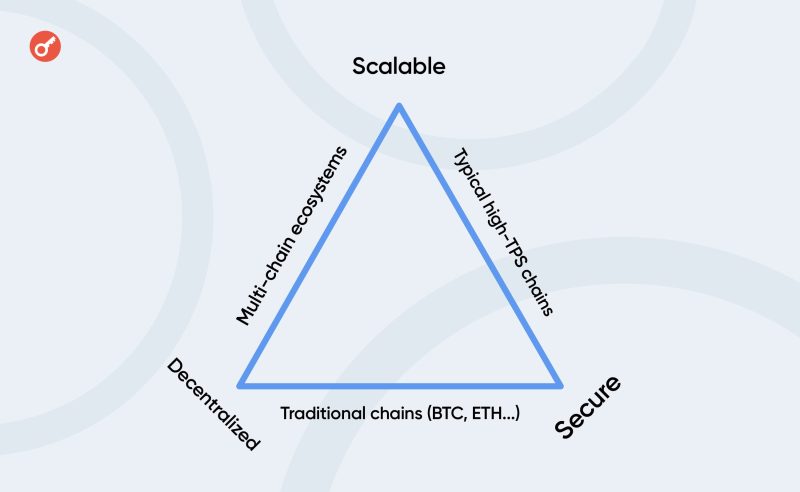
According to this theory, blockchains can either be secure and decentralised but slow, like bitcoin, or fast and secure but overly centralised, like BSC.
It is the blockchain trilemma that largely determines the direction of the industry, as most infrastructure projects aim to overcome the limitations it describes. For example, the Lightning Network was developed to compensate for bitcoin’s low bandwidth, while Ethereum has grown into dozens of layer 2 networks due to high fees.








